Publish at Scribd or explore others:
Monday, December 8, 2008
Tuesday, November 25, 2008
Wednesday, September 24, 2008
OS-Assignment
1. Token Ring is a very old and outdated LAN protocol in comparison to Ethernet. If I remember correctly, Token Ring was developed years ago by IBM, after which the IEEE committee made it a standard. Speeds of up to 16Mbps are possible with Token Ring networks, providing safer methods of data transfer between nodes when compared to Ethernet.
source: http://searchnetworking.techtarget.com/loginMembersOnly/1,289498,sid7_gci1112642,00.html?NextURL=http%3A//searchnetworking.techtarget.com/expert/KnowledgebaseAnswer/0%2C289625%2Csid7_gci1112642%2C00.html?referrer=SEO_MO|www.google.com.ph_ER_1112642
2.The implicatiions of passing logon procedures, user IDs, and passwords openly on the network are great risk to protect critical information on the network. Appropriate access controls assist to protect information processed and stored in computer systems. The organisation's system security policy must clearly define the needs of each user or group to access systems, applications and data. The file-access rights should be configured according to business requirements and the "need to know" principle.
3.The importance of computer networking to achieve resource sharing and data sharing is widely recognized. Local networking to achieve high performance and reliability is inevitable for the future. As cost of logic and memory decreases, the cost of communications resources become increasingly significant and these resources must be increasingly shared. This heightens the possibility of deadlocks due to this sharing.
- their must be a mutual exclusive access in the network.
- their must be a condition for holding non-sharable resources.
- any request for certain files inn the network must be allocated, but it cannot request another resources unless it releases the resource that it holds.
- before requesting resources, we first check wheter they arre available or not to prevent hold and wait state.
In an apparatus having a network including successive stages of cross-point switches which collectively interconnect a plurality of nodes external to said network, wherein at least one message is carried between one of the nodes and one of the cross-point switches over a route through said network, a method for preventing routing deadlocks from occurring in the network which comprises the steps of: creating a graphical representation of the network; searching for the existence of cycles within the graphical representation; partitioning the graphical representation into at a first subgraph and a second subgraph if cycles exist in the graphical representation; searching for the existence of edges directed from the first subgraph to the second subgraph; and removing the edges directed from the first subgraph to the second subgraph. Preferably the step of partitioning the network into at a first subgraph and a second subgraph is performed such that the first subgraph and the second subgraph have an equal number of vertices, a number of directed edges from the first subgraph to the second subgraph is minimized so as to minimize the number of routes prohibited, and a set of partition constraints are satisfied. The method is recursively applied to the first subgraph and then the second subgraph, thereby removing all of the deadlock prone cycles in the network while minimizing the number of routes prohibited due to remove edges.
The problem of detecting process deadlocks is common to transaction oriented computer systems which allow data sharing. Several good algorithms exist for detecting process deadlocks in a single location facility. However, the deadlock detection problem becomes more complex in a geographically distributed computer network due to the fact that all the information needed to detect a deadlock is not necessarily available in a single node, and communications may lead to synchronization problems in getting an accurate view of the network state.
Two algorithms are then presented for detecting deadlocks in a computer network which allows processes to wait for access to a portion of a database, or a message from another process. The first algorithm presented is based on the premise that there is one control node in the network, and this node has primary responsibility for detecting process deadlocks. The second, and recommended, algorithm distributes the responsibility for detecting deadlocks among the nodes in which the involved processes and resources reside. Thus a failure of any single node has limited effect upon the other node in the network.
Routing algorithms used in wormhole switched networks must all provide a solution to the deadlock problem. If the routing algorithm allows deadlock cycles to form, then it must provide a deadlock recovery mechanism. Because deadlocks are anomalies that occur while routing, the deadlock recovery mechanism should not allocate any expensive hardware resources for the sake of handling such a rare event. Rather, it should only dedicate a minimal set of required resources to the recovery process in order to engage most of the hardware resources to the task of routing normal packets. This paper proposes a new deadlock recovery mechanism to be used with the True Fully Adaptive Routing algorithm. The new deadlock recovery mechanism takes advantage of the concept behind wormhole switching. The scheme is efficient in terms of hardware requirements, causes fewer deadlocks and can compete with other expensive deadlock recovery schemes.
Source: http://www.freepatentsonline.com/6065063.html
http://oai.dtic.mil/oai/oai?verb=getRecord&metadataPrefix=html&identifier=ADA047025
http://ieeexplore.ieee.org/Xplore/login.jsp?url=/iel5/6712/17967/00830311.pdf?temp=x
4.I Would Prefer A switch (switching hub) in the context of networking refers to a device which filters and forwards data packets across a network.
Unlike a standard hub which simply replicates what it receives on one port onto all the other ports, a switching hub keeps a record of the MAC addresses of the devices attached to it.
When the switch receives a data packet, it forwards the packet directly to the recipient device by looking up the MAC address.
A network switch can utilise the full throughput potential of a networks connection for each device making it a natural choice over a standard hub.
In other words, say for instance you had a network of 5 PCs and a server all connected with 10Mbps UTP cable, with a hub the throughput (10Mbps) would be shared between each device, with a switch each device could utilise the full 10Mbps connection.
When using a switch instead of a hub it is common place to create a faster throughput connection between the switch and the server (backbone).
For example if you had 10 PCs connected to the switch with 10Mbps cable then it would improve performance to use a 100Mbps connection from the switch to the server.
Source: http://www.helpwithpcs.com/jargon/network-switch.htm
source: http://searchnetworking.techtarget.com/loginMembersOnly/1,289498,sid7_gci1112642,00.html?NextURL=http%3A//searchnetworking.techtarget.com/expert/KnowledgebaseAnswer/0%2C289625%2Csid7_gci1112642%2C00.html?referrer=SEO_MO|www.google.com.ph_ER_1112642
2.The implicatiions of passing logon procedures, user IDs, and passwords openly on the network are great risk to protect critical information on the network. Appropriate access controls assist to protect information processed and stored in computer systems. The organisation's system security policy must clearly define the needs of each user or group to access systems, applications and data. The file-access rights should be configured according to business requirements and the "need to know" principle.
3.The importance of computer networking to achieve resource sharing and data sharing is widely recognized. Local networking to achieve high performance and reliability is inevitable for the future. As cost of logic and memory decreases, the cost of communications resources become increasingly significant and these resources must be increasingly shared. This heightens the possibility of deadlocks due to this sharing.
- their must be a mutual exclusive access in the network.
- their must be a condition for holding non-sharable resources.
- any request for certain files inn the network must be allocated, but it cannot request another resources unless it releases the resource that it holds.
- before requesting resources, we first check wheter they arre available or not to prevent hold and wait state.
In an apparatus having a network including successive stages of cross-point switches which collectively interconnect a plurality of nodes external to said network, wherein at least one message is carried between one of the nodes and one of the cross-point switches over a route through said network, a method for preventing routing deadlocks from occurring in the network which comprises the steps of: creating a graphical representation of the network; searching for the existence of cycles within the graphical representation; partitioning the graphical representation into at a first subgraph and a second subgraph if cycles exist in the graphical representation; searching for the existence of edges directed from the first subgraph to the second subgraph; and removing the edges directed from the first subgraph to the second subgraph. Preferably the step of partitioning the network into at a first subgraph and a second subgraph is performed such that the first subgraph and the second subgraph have an equal number of vertices, a number of directed edges from the first subgraph to the second subgraph is minimized so as to minimize the number of routes prohibited, and a set of partition constraints are satisfied. The method is recursively applied to the first subgraph and then the second subgraph, thereby removing all of the deadlock prone cycles in the network while minimizing the number of routes prohibited due to remove edges.
The problem of detecting process deadlocks is common to transaction oriented computer systems which allow data sharing. Several good algorithms exist for detecting process deadlocks in a single location facility. However, the deadlock detection problem becomes more complex in a geographically distributed computer network due to the fact that all the information needed to detect a deadlock is not necessarily available in a single node, and communications may lead to synchronization problems in getting an accurate view of the network state.
Two algorithms are then presented for detecting deadlocks in a computer network which allows processes to wait for access to a portion of a database, or a message from another process. The first algorithm presented is based on the premise that there is one control node in the network, and this node has primary responsibility for detecting process deadlocks. The second, and recommended, algorithm distributes the responsibility for detecting deadlocks among the nodes in which the involved processes and resources reside. Thus a failure of any single node has limited effect upon the other node in the network.
Routing algorithms used in wormhole switched networks must all provide a solution to the deadlock problem. If the routing algorithm allows deadlock cycles to form, then it must provide a deadlock recovery mechanism. Because deadlocks are anomalies that occur while routing, the deadlock recovery mechanism should not allocate any expensive hardware resources for the sake of handling such a rare event. Rather, it should only dedicate a minimal set of required resources to the recovery process in order to engage most of the hardware resources to the task of routing normal packets. This paper proposes a new deadlock recovery mechanism to be used with the True Fully Adaptive Routing algorithm. The new deadlock recovery mechanism takes advantage of the concept behind wormhole switching. The scheme is efficient in terms of hardware requirements, causes fewer deadlocks and can compete with other expensive deadlock recovery schemes.
Source: http://www.freepatentsonline.com/6065063.html
http://oai.dtic.mil/oai/oai?verb=getRecord&metadataPrefix=html&identifier=ADA047025
http://ieeexplore.ieee.org/Xplore/login.jsp?url=/iel5/6712/17967/00830311.pdf?temp=x
4.I Would Prefer A switch (switching hub) in the context of networking refers to a device which filters and forwards data packets across a network.
Unlike a standard hub which simply replicates what it receives on one port onto all the other ports, a switching hub keeps a record of the MAC addresses of the devices attached to it.
When the switch receives a data packet, it forwards the packet directly to the recipient device by looking up the MAC address.
A network switch can utilise the full throughput potential of a networks connection for each device making it a natural choice over a standard hub.
In other words, say for instance you had a network of 5 PCs and a server all connected with 10Mbps UTP cable, with a hub the throughput (10Mbps) would be shared between each device, with a switch each device could utilise the full 10Mbps connection.
When using a switch instead of a hub it is common place to create a faster throughput connection between the switch and the server (backbone).
For example if you had 10 PCs connected to the switch with 10Mbps cable then it would improve performance to use a 100Mbps connection from the switch to the server.
Source: http://www.helpwithpcs.com/jargon/network-switch.htm
Thursday, January 31, 2008
DVD Recording
This is the last step in the DVD creation process.
With our DVD Project having been Compiled, there are a set of files that DVD-lab has prepared for you in the Output folder as set in the Compile process. At this point, the DVD Author has choices as to how to convert this set of files into a DVD master disc. You can either use the DVD-lab built-in recording module or you can choose to use a third party DVD recording software such as Nero, Prassi, Gear, etc...
It is common that you are supplied with a DVD recording software that was bundled with your DVD-R/DVD+R burner. This software may be better optimized for your particular drive. The DVD-lab built-in DVD recording module is a general ASPI writing application and should work fine. In an ideal world, either one would work equally well.
DVD-lab Disc record window
The DVD-lab Disc record window is automatically detached. That means it runs as a separate process independent from DVD-lab, you could even close DVD-lab and the recording will continue.
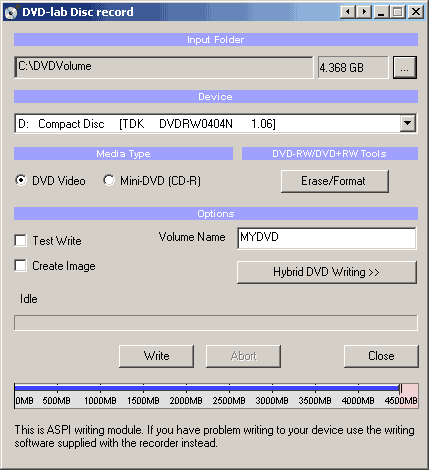
Here are some of the parameter choices for the DVD-lab Disc record window.
Input Folder
The Input Folder is the same as the Output folder in Compile. That means this is the folder where the VIDEO_TS and AUDIO_TS folders are expected to be.
Device
The DVD recording drive you want to write to, presented as the O/S recognizes it.
Media Type
Set if you want to burn DVD Video or a Mini-DVD.Mini-DVD is a DVD format burned on the CD-R. Obviously you can put far less data on a CD-R (about 700 MB) than on DVD (4.3 GB)

The size indicator on the bottom can help you to determine how much data you can record to the disc. You have to keep your data below the red area.

Note: While you will be able to play the CD-R on a computer not all standalone players will be able to play the Mini-DVD. In fact such format is not officially supported. The reason is that CD's have far less density of data so in order to play the large DVD video bitrate they have to spin much faster than DVD. Not all DVD drives in players are ready for this so the functionality to DVD files from CD-R is often simply disabled. However a number of Asian or re-branded Asian US models of players use a standard PC type of DVD drive which allows for fast spin of CD.
DVD-RW/DVD+RW Tools
For those using a re-writable media, the DVD-RW needs to be formatted if they were already used - click the Erase/Format button to do this. The more common DVD-R media do not need any formatting.
The DVD-RW and +RW needs to be finalized after writing. This takes quite a large amount of time on RW media. Please be patient until this important process is completed.
Options
Test Write checkboxUse this option by checking the Test Write checkbox to have DVD-lab do a trial run at writing a DVD. This option does not write anything to disk or your hard drive, it merely goes through the motions to insure that all of the content and menus within the DVD project are correctly prepared and defined.
Volume Name inputEnter here a name for the DVD volume that will appear when placed in a computer drive. A standalone DVD player just ignores this.
Create Image checkboxYou can choose to have DVD-lab create a large file on your hard drive which is an the image of a DVD disc instead of burning. The result will be one big IMG file. That IMG file can be used with a number of third party DVD recording software to replicate a DVD disc from this image file, as many times as you like, whenever you like. Some software will look for a ISO file name extension, if so, just rename the file to a .ISO extension. This method has the advantage of speed as the DVD image is all prepared on your hard drive, it is then a just matter of how fast your DVD burner drive will burn that image.
Hybrid DVD Writing buttonYou can add additional files and folders to the DVD master disc with the Hybrid DVD Writing option. What this option will do is setup an alternate filesystem on the DVD master disc which is called an ISO filesystem. The ISO format is what a standard CD uses while the DVD video is in UDF/ISO. This is perfectly DVD "legal" as the DVD player doesn't know or care about this ISO filesystem's contents, it just looks for a UDF filesystem.
It doesn't matter at all what the content or nature of these files are. They are just files, not Windows or Mac or Linux files, just files. As they are recorded into the ISO file system domain, they are available on any computer with a DVD drive. This offers the DVD-lab Author some creative options for bonus content that would be available to a computer user on any O/S that supports a DVD drive.

For example, you can create an autorun project in Multimedia Builder and record it to DVD as an extra feature when used on PC. HTML based content may be placed here as well, be sure to indicate to your computer users where to find your HTML starting page (ex: index.html).
Note: The space used by the Hybrid DVD Writing option counts in the entire Project space value. You only get so much space on a DVD (4.7G), this option uses part of that. Do the math to be sure you have room for this extra area.
Write buttonAs expected, click this button to start the DVD writing (burn) process.
Note: It is not recommended to do any work on the computer during DVD writing. Things like reading/writing to hard-drive may easily ruin your DVD-R. Try to let the burning process be the only thing your computer is running until it is completed.
With our DVD Project having been Compiled, there are a set of files that DVD-lab has prepared for you in the Output folder as set in the Compile process. At this point, the DVD Author has choices as to how to convert this set of files into a DVD master disc. You can either use the DVD-lab built-in recording module or you can choose to use a third party DVD recording software such as Nero, Prassi, Gear, etc...

It is common that you are supplied with a DVD recording software that was bundled with your DVD-R/DVD+R burner. This software may be better optimized for your particular drive. The DVD-lab built-in DVD recording module is a general ASPI writing application and should work fine. In an ideal world, either one would work equally well.
DVD-lab Disc record window
The DVD-lab Disc record window is automatically detached. That means it runs as a separate process independent from DVD-lab, you could even close DVD-lab and the recording will continue.

Here are some of the parameter choices for the DVD-lab Disc record window.
Input Folder
The Input Folder is the same as the Output folder in Compile. That means this is the folder where the VIDEO_TS and AUDIO_TS folders are expected to be.
Device
The DVD recording drive you want to write to, presented as the O/S recognizes it.
Media Type
Set if you want to burn DVD Video or a Mini-DVD.Mini-DVD is a DVD format burned on the CD-R. Obviously you can put far less data on a CD-R (about 700 MB) than on DVD (4.3 GB)

The size indicator on the bottom can help you to determine how much data you can record to the disc. You have to keep your data below the red area.

Note: While you will be able to play the CD-R on a computer not all standalone players will be able to play the Mini-DVD. In fact such format is not officially supported. The reason is that CD's have far less density of data so in order to play the large DVD video bitrate they have to spin much faster than DVD. Not all DVD drives in players are ready for this so the functionality to DVD files from CD-R is often simply disabled. However a number of Asian or re-branded Asian US models of players use a standard PC type of DVD drive which allows for fast spin of CD.
DVD-RW/DVD+RW Tools
For those using a re-writable media, the DVD-RW needs to be formatted if they were already used - click the Erase/Format button to do this. The more common DVD-R media do not need any formatting.
The DVD-RW and +RW needs to be finalized after writing. This takes quite a large amount of time on RW media. Please be patient until this important process is completed.
Options
Test Write checkboxUse this option by checking the Test Write checkbox to have DVD-lab do a trial run at writing a DVD. This option does not write anything to disk or your hard drive, it merely goes through the motions to insure that all of the content and menus within the DVD project are correctly prepared and defined.
Volume Name inputEnter here a name for the DVD volume that will appear when placed in a computer drive. A standalone DVD player just ignores this.
Create Image checkboxYou can choose to have DVD-lab create a large file on your hard drive which is an the image of a DVD disc instead of burning. The result will be one big IMG file. That IMG file can be used with a number of third party DVD recording software to replicate a DVD disc from this image file, as many times as you like, whenever you like. Some software will look for a ISO file name extension, if so, just rename the file to a .ISO extension. This method has the advantage of speed as the DVD image is all prepared on your hard drive, it is then a just matter of how fast your DVD burner drive will burn that image.
Hybrid DVD Writing buttonYou can add additional files and folders to the DVD master disc with the Hybrid DVD Writing option. What this option will do is setup an alternate filesystem on the DVD master disc which is called an ISO filesystem. The ISO format is what a standard CD uses while the DVD video is in UDF/ISO. This is perfectly DVD "legal" as the DVD player doesn't know or care about this ISO filesystem's contents, it just looks for a UDF filesystem.
It doesn't matter at all what the content or nature of these files are. They are just files, not Windows or Mac or Linux files, just files. As they are recorded into the ISO file system domain, they are available on any computer with a DVD drive. This offers the DVD-lab Author some creative options for bonus content that would be available to a computer user on any O/S that supports a DVD drive.

For example, you can create an autorun project in Multimedia Builder and record it to DVD as an extra feature when used on PC. HTML based content may be placed here as well, be sure to indicate to your computer users where to find your HTML starting page (ex: index.html).
Note: The space used by the Hybrid DVD Writing option counts in the entire Project space value. You only get so much space on a DVD (4.7G), this option uses part of that. Do the math to be sure you have room for this extra area.
Write buttonAs expected, click this button to start the DVD writing (burn) process.
Note: It is not recommended to do any work on the computer during DVD writing. Things like reading/writing to hard-drive may easily ruin your DVD-R. Try to let the burning process be the only thing your computer is running until it is completed.
Subscribe to:
Posts (Atom)



